Comparison between NHP and SPA
Note: The following content is extracted from the journal paper “AHAC: Advanced Network-Hiding Access Control Framework” published in Volume 14, Issue 13 of the journal Applied Sciences in 2024. It is worth noting that the AHAC framework is a key component of the NHP (OpenNHP) technology system.
1. Advantage Comparison
NHP combines the Noise protocol, key pairs, and ECDH algorithm to provide a robust bidirectional authentication mechanism. Compared to traditional methods, NHP offers significant advantages in terms of performance, scalability, and security. It supports multiple programming languages (such as C/C++, Python, Java, and Go) and provides a highly scalable architecture that enhances device authentication, defends against replay attacks, and fully addresses IP amplification issues. NHP is particularly well-suited for scenarios requiring strong authentication and encryption, such as enterprise IAM systems and secure resource access. It optimizes performance and enhances high availability, ensuring seamless compatibility and high security in complex environments. In contrast, while SPA has certain strengths, it still cannot match NHP in security, performance, and scalability.
| SPA | NHP | |
|---|---|---|
| Development Language | C, C++ | C/C++, Python, Java, Go |
| Communication | Single-packet authorization | Noise protocol, ECDH |
| Architecture | Complexity, encrypted packets, firewall | Advanced, scalable, Noise protocol |
| Authentication | UDP port knocking, IP amplification issue | Device fingerprint, UDP and TCP port knocking |
| Cryptography Framework | RSA, AES | Noise protocol, ECDH |
| Performance | Moderate overhead, efficient | Optimized, minimal overhead |
| Network Hiding Capability | Only service/application port | Domain name, IP, and port |
| Availability | High load | High availability, scalable clusters |
| Scalability | Complex implementation | FIDO+NHP, highly scalable, easy integration |
| Compatibility | Various systems, potential integration needed | High, cross-platform, future-oriented |
| Security | Strong encryption, key management risk | Address hiding, mutual authentication |
| Use Cases | High-security scenarios | Scalable, high-security environments |
2. Performance Comparison
2.1 Encryption Algorithm Overhead
SPA uses the RSA encryption algorithm, while NHP utilizes ECC encryption. We compared the cost-effectiveness of RSA and ECC based on security strength and key length, as shown in the table below. Under the same security standards, the key length of ECC is significantly shorter than that of RSA. Additionally, the ciphertext generated by RSA message signatures is roughly equal to the key length. Therefore, when verifying network message identities, NHP uses shorter ECC random keys (32 bytes or 64 bytes) for ECDH exchange instead of transmitting larger RSA2048 message signatures (256 bytes) for validation. This not only reduces computational overhead but also efficiently saves valuable bandwidth resources. This strategy highlights that NHP has a significant advantage over SPA in terms of improving system efficiency and resource utilization.
| Security Strength (bits) | SPA (Minimum Public Key Length (bits)) | NHP (Minimum Public Key Length (bits)) | NHP vs SPA (Key Length Ratio) | Validity Period |
|---|---|---|---|---|
| 80 | 1024 | 160-223 | 1:6 | Until 2010 |
| 112 | 2048 | 224-255 | 1:9 | Until 2010 |
| 128 | 3072 | 256-383 | 1:12 | After 2031 |
| 192 | 7680 | 384-511 | 1:20 | |
| 256 | 15360 | 512+ | 1:30 |
We measured the encryption and decryption times of RSA and ECC through experiments, with the detailed results shown in the table below. The experiments increased the number of encryption and decryption cycles to test the performance of both algorithms under different conditions. The results show that although the encryption and decryption times for both RSA and ECC increased with the number of cycles, the time overhead for ECC remained consistently much lower than that of RSA. Especially as the number of cycles increased, the advantage of ECC became more pronounced, with RSA’s time overhead reaching up to 800 times that of ECC. This significant gap demonstrates that NHP is vastly superior to SPA in terms of encryption and decryption efficiency, providing strong support for selecting a more efficient encryption algorithm in practical applications.
| Cycle Times | SPA | NHP |
|---|---|---|
| 1 | 0.34s | 687us |
| 10 | 2.48s | 3.60ms |
| 100 | 27.54s | 0.03s |
| 200 | 61.18s | 0.06s |
| 500 | 136.23s | 0.16s |
| 1000 | 287.61s | 0.32s |
| 10000 | 2832.42s | 3.81s |
2.2 Performance Overhead
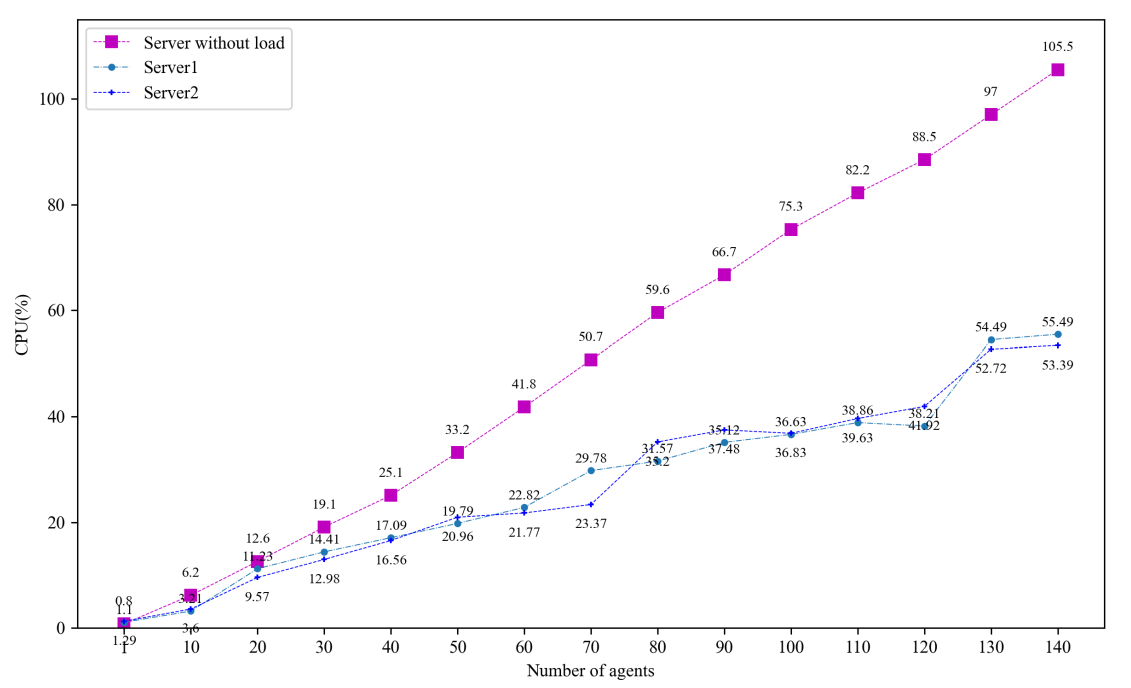
To comprehensively evaluate the performance of NHP, we set up the experimental environment shown in the figure below and conducted load performance tests for both NHP and SPA. The environment consists of two main areas: the Agent deployment area and the network stealth deployment area.
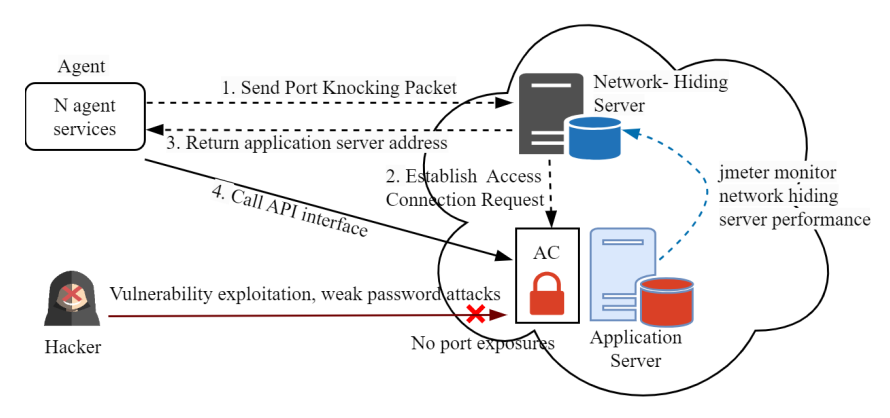
In the network stealth deployment area, we integrated a network stealth server and an application server as key components. To ensure the stability and consistency of the test environment, we selected three machines with identical configurations, each equipped with a 4-core CPU and 8GB of memory. In the agent deployment area, we launched n agent services that communicated with the network stealth server at a frequency of sending a port knocking request per second. At the same time, JMeter components were deployed on the network stealth server to simulate and monitor its performance. On the application server side, JMeter services were also deployed to track the performance resource consumption of the network stealth server in real time. With this setup, we were able to comprehensively monitor and compare the performance of NHP and SPA.
While maintaining the consistency of the experimental environment, we selected 1, 10, 20, 30, 40, and 50 agents according to the deployment plan and conducted performance tests for NHP and SPA. The test results are shown in Table 4, where the horizontal axis represents the number of agents involved in the experiment, and the vertical axis displays the variation in CPU utilization during the test period. With this setup, we can visually observe the different performance of NHP and SPA in terms of CPU resource consumption as the number of agents increases.
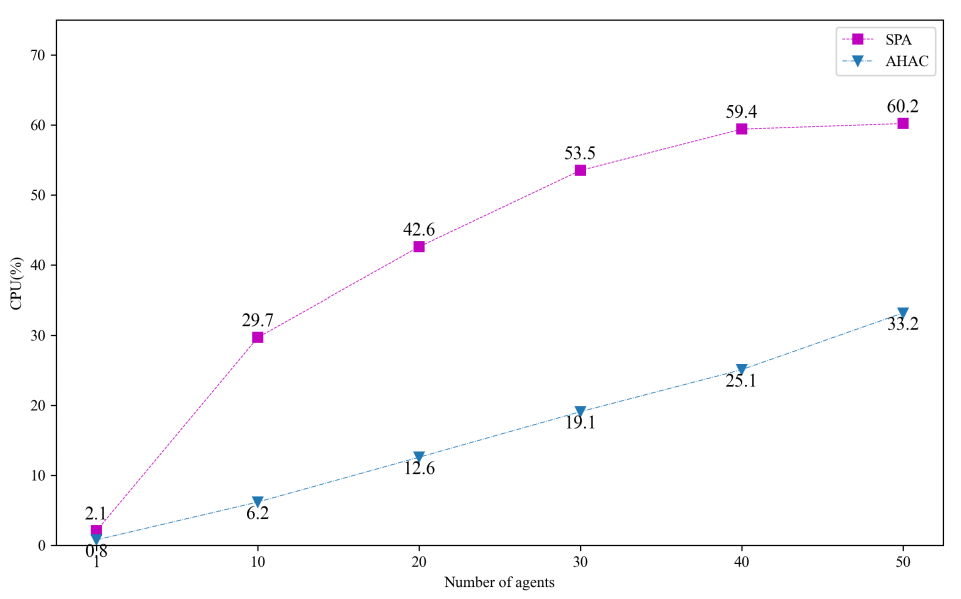
The experimental results show that as the number of agents increases, the CPU load for both NHP and SPA rises. However, with further increases in the number of agents, the performance advantage of NHP becomes more pronounced, with its CPU load remaining approximately half that of SPA, demonstrating a significant improvement in efficiency.
(Note: Although theoretically NHP performance should be approximately 1000 times better than SPA, actual tests showed only about a 1-fold improvement. The primary factors contributing to this discrepancy include the significant impact of network overhead on performance, performance losses due to the garbage collection mechanism, and differences in hardware environments. Additionally, despite choosing the memory-safe Go language for code security and encryption algorithm implementation, its garbage collection mechanism also had a certain impact on performance.)
3. High Availability Comparison
NHP achieves high availability for zero trust services through a distributed architecture, ensuring that the port knocking module and the access control module are deployed on different hosts to avoid resource contention and enhance elastic scaling. Even in the event of a failure, seamless service switching can maintain system functionality and response speed. This design enhances the robustness and stability of the system, reducing the impact of service failures on the overall system, as shown in the figure below.
NHP supports horizontal elastic scaling for port knocking verification services, allowing the number of service instances to be dynamically adjusted based on real-time load. This feature provides high flexibility and scalability, ensuring that services remain responsive and stable even under high load. Each service instance can handle port knocking requests and maintain business sessions, which not only enhances processing capacity but also improves fault tolerance, ensuring business continuity and stability. According to the test results, NHP significantly outperforms SPA in terms of high availability.
4. Scalability Comparison
Although NHP is designed to provide a trusted, controllable, reliable, and verifiable foundation for data communication, it also needs to have good scalability to adapt to various customization needs due to the diversity and complexity of communication scenarios and environments. The scalability of NHP is reflected in several aspects:
Its bidirectional communication mechanism, compared to SPA’s unidirectional port knocking mechanism, offers richer expansion capabilities. It can hide the true IP addresses of resources and support key exchanges before and after data communication, enhancing the security of privacy computing and data flow scenarios.
Through the Authorization Service Provider (ASP) interface, NHP can pass resource request contents to the ASP, enabling stricter identity authentication and access control.
NHP’s resource identifiers support arbitrary string formats, including Chinese and English characters and symbols, providing stronger descriptive capabilities for data resources. It also has DNS resolution functionality, offering more secure, encrypted, and private domain name resolution services.
Therefore, NHP’s scalable architecture covers typical application scenarios such as integration with DNS and FIDO.
4.1 Integration with DNS
DNS is a crucial foundational service for internet operations, but its security has long been overlooked. Due to the use of the unreliable UDP protocol, there are numerous security vulnerabilities, such as DNS hijacking and denial-of-service attacks. Therefore, strengthening DNS security is essential. By integrating network stealth technology, DNS resolution is conducted through a bidirectional encrypted channel, ensuring confidentiality and tamper-resistance. Additionally, only authenticated users are allowed to perform resolution, effectively defending against DDoS attacks and hijacking. The specific implementation is shown in the figure below, and our approach significantly enhances DNS security, providing users with a more reliable DNS service.
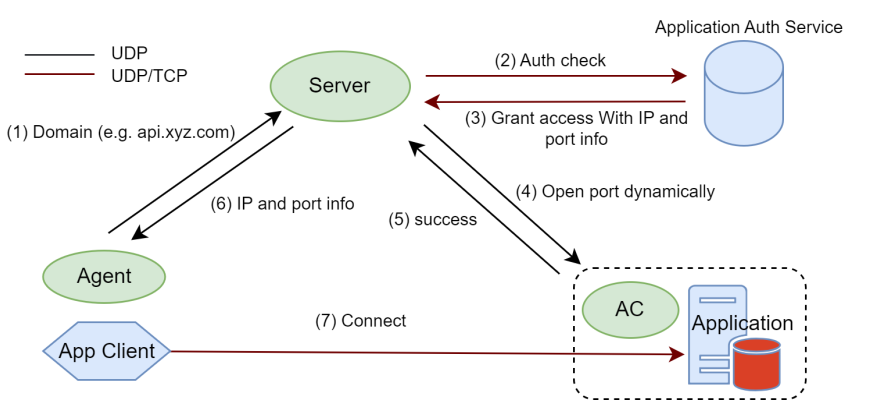
(1) The Agent (such as a client, browser, etc.) initiates a request to the Network-Hiding Server (i.e., Server) using a domain name.
(2) Once the Server receives the domain name data packet request from the Agent, it immediately sends an authentication query request to the application authentication server to verify the legality and permissions of the request.
(3) Upon receiving the authentication request message from the Server, the authentication server undergoes a strict verification process. Once the identity is confirmed to be authentic and valid, it grants access permissions. Subsequently, the authentication server promptly replies to the Server with an authorized access credential containing critical information such as the real IP address and port number of the target resource.
(4) After successfully passing the authentication query, the Server quickly initiates an access request to the access control system of the target resource. This request aims to ensure that the Agent can access the required target resource seamlessly, facilitating subsequent operations.
(5) Upon receiving the access request from the Server, the access control system immediately performs a rigorous verification procedure. This process ensures that the requested target resource matches the protected resource exactly, thereby ensuring the security and reliability of the system. Once verified, the AC system swiftly establishes a connection channel from the Agent to the protected resource, allowing unobstructed access.
(6) Once the AC system successfully grants access to the Agent, the Server promptly confirms this operation and returns the IP address and port information of the target resource. These details are then quickly transmitted to the Agent, enabling it to accurately locate and access the protected resource (i.e., Application).
(7) After receiving the IP address and port information of the Application, the Agent immediately initiates normal business access to the Application, achieving efficient and secure resource interaction.
4.2 Integration with FIDO
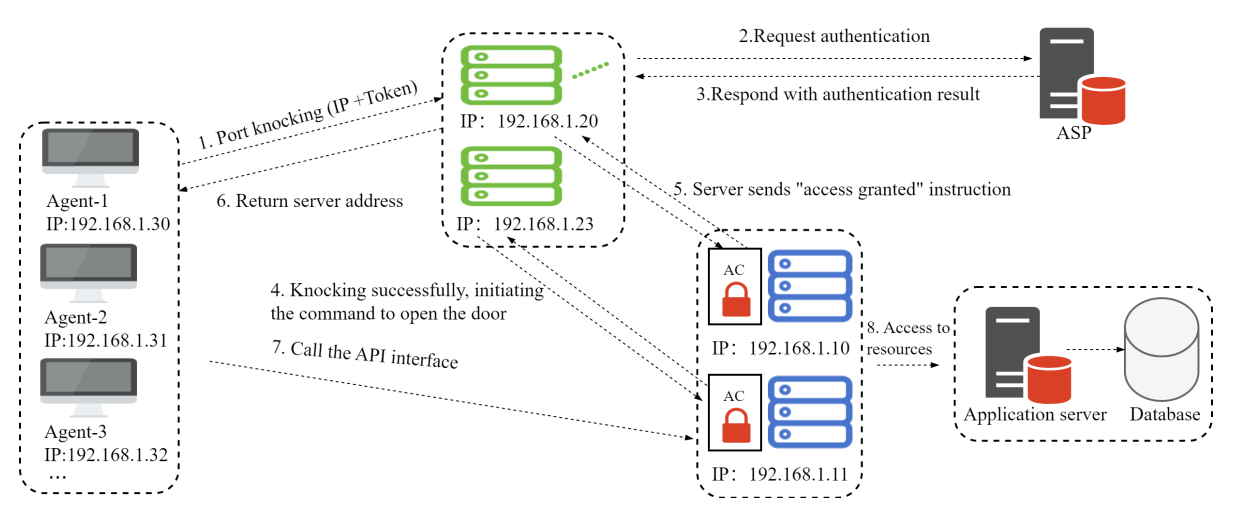
Although FIDO performs exceptionally well in web authentication, potential vulnerabilities in servers can still be exploited by hackers to bypass FIDO authentication and directly invade servers for data theft or damage. Integrating FIDO with NHP can effectively address the shortcomings of FIDO in vulnerability protection, providing a more comprehensive defense solution for internet exposure. The specific implementation is shown in the figure below, with detailed implementation steps as follows.
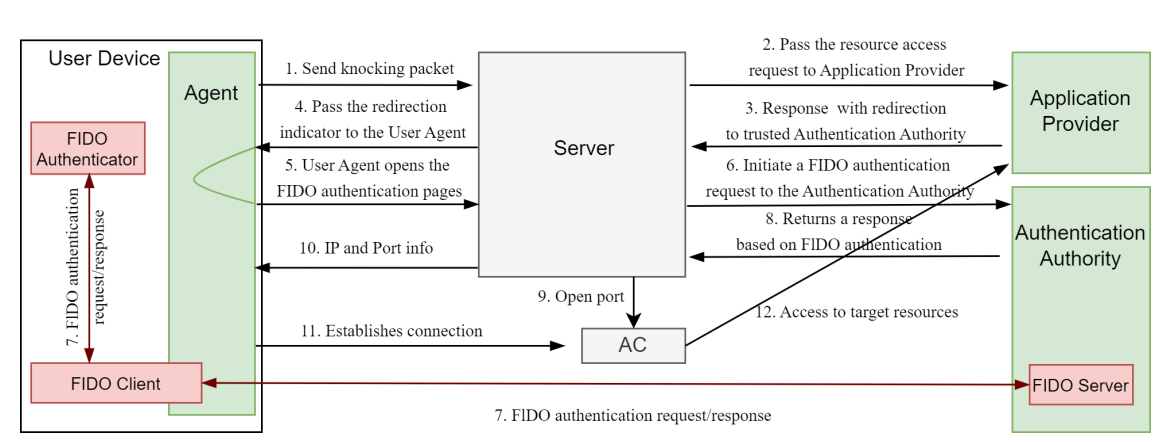
(1) The User Agent (i.e., Agent) sends a Port Knocking packet to the Network-Hiding Server (i.e., Server) aiming to attempt access to sensitive resources within sessions that have been authenticated but with relatively lower assurance levels.
(2) Upon receiving the Port Knocking packet, the Server forwards the resource access request to the Application Provider.
(3) The Application Provider responds and sends a reply message to the Server while redirecting the Port Knocking message to a trusted authentication authority to request a higher assurance FIDO-based authentication.
(4) After receiving the Application Provider’s response, the Server passes the redirection indicator to the Agent.
(5) Upon receiving the redirection message, the Agent directly opens the FIDO authentication page.
(6) The Server, upon receiving the Agent’s FIDO authentication page, promptly initiates a FIDO authentication request to the authentication authority.
(7) The FIDO server completes the FIDO request and responds after receiving the request message.
(8) The authentication authority, after a rigorous FIDO verification process, returns a FIDO-based authentication response to the Server.
(9) Once the FIDO identity is confirmed to be authentic and valid, and the authentication is successful, the Server requests the Access Control (i.e., AC) system to open the Application Provider’s port to accept the Agent’s connection.
(10) The Server notifies the Agent of the successful authentication and provides the IP/port for resource access.
(11) The AC system successfully grants access permission to the Agent.
(12) The Agent establishes a connection with the Application Provider to access the resources.
5. Compatibility Comparison
Compared to the SPA protocol, a key goal of NHP is to ensure good compatibility with both the domestic zero trust standards and the innovation-driven environment. In terms of encryption algorithms, NHP supports international cryptographic algorithms (such as RSA, SHA256, AES) as well as national cryptographic algorithms (such as SM2, SM3, SM4), and can adjust encryption time based on the length of the packet header. Regarding hardware and software compatibility, NHP is adapted to major domestic and international CPU hardware and operating systems, including Kunpeng, x86, Loongson, and Shenwei. Additionally, NHP complies with the forthcoming national standard “Information Security Technology - Zero Trust Reference Architecture,” ensuring compatibility with this standard, as shown in the figure below.